Interpretation of the “Personal Information Protection Law of the People’s Republic of China”
On August 20, 2021, the 30th meeting of the Standing Committee of the 13th National People’s Congress passed the “Personal Information Protection Law of the People’s Republic of China” (hereinafter referred to as the “Personal Information Protection Law”). Since October 2020, the “Personal Information Protection Law” will be officially implemented on November 1, 2021 after three deliberations and revisions.
1. Background introduction
1.1 Release background
The latest data show that the overall scale of Chinese Internet users in 2020 has accounted for one-fifth of the global Internet users, and the number of Chinese Internet users in 2020 will be 989 million. There are 4.43 million internet websites and 3.02 million mobile applications. Since 2021, the Cyberspace Administration of China has tested more than ten types of mobile phone applications such as map navigation, sports and fitness, and short videos. 351 apps were notified for collecting personal information illegally, and 25 apps were taken off the shelves for collecting and using personal information in serious violations of laws and regulations.
“In order to respond to the calls and expectations of the broad masses of the people in a timely manner, and to implement the requirements of the Party Central Committee, it is of great significance to formulate a special law on the protection of personal information, so as to realize, maintain and develop the rights and interests of the broad masses of people’s personal information. “Liu Junchen, deputy director of the Legal Work Committee of the Standing Committee of the National People’s Congress, said that the formulation of a personal information protection law is an objective requirement to further strengthen the legal protection of personal information protection, a practical need to maintain a good ecology in cyberspace, and an important measure to promote the healthy development of the digital economy. .
Judging from the current promulgated laws, although some of the contents are related to the protection of personal information, in social practice, the application of these laws mostly stipulates relatively principles and cannot meet the various urgent needs of citizens for the protection of personal information. In addition, look at other laws and regulations and normative documents, such as the “Decision on Strengthening the Protection of Network Information”, “Provisions on the Protection of Personal Information of Telecommunications and Internet Users”, “Information Security Technology and Personal Information Security Regulations” (GB/T 35273—2020) and other regulations. Although it plays a strong reference value for compliance in judicial cases, it also has a certain degree of lag and cannot meet the compliance needs of various Internet companies. In recent years, cases of abuse of personal information have continued to emerge, which has also brought greater challenges to judicial and administrative supervision departments.
1.2 Development history
Since 2003, my country has initiated legislative procedures for the protection of personal information. After more than ten years of continuous exploration, the personal information protection legislation has gradually become more perfect. The following is a further explanation from several important time nodes:
In 2003, the “Personal Information Protection Law” expert proposal draft began to be drafted, and it was completed in early 2005;
In 2009, Article 7 of the “Criminal Law Amendment (7)” included the illegal provision and acquisition of citizens’ personal information into the criminal law;
In 2013, the “Provisions on the Protection of Personal Information of Telecommunications and Internet Users” defined “citizens’ personal Electronic information” and clarified the principles and relevant rules for information collection and use;
In 2017, the implementation of the “Cyber Security Law” further defined “citizens’ personal information”, made clear provisions for users’ “informed consent”, and made clear requirements for “network operators”;
In 2020, the “Civil Code” emphasizes “people-oriented” and strengthens the protection of citizens’ privacy and personal information;
In June 2020, the Standing Committee of the National People’s Congress adjusted the 2020 legislative work plan, and the draft personal information protection law will be submitted for deliberation.
The “Personal Information Protection Law” was included in the legislative agenda of the Standing Committee of the National People’s Congress in 2018 for the next five years. It has gone through from the first review in 2020 to the second and third reviews in 2021. The specific content of the “Personal Information Protection Law” Also constantly changing.
1.3 Legal Map
This article starts from five levels of national laws, administrative regulations, judicial interpretations, departmental regulations, and technical specifications, sorts out domestic data security and personal information protection related systems, and organizes a visually viewable “Legal Map of China’s New Data Order”.
Domestic security work adheres to the overall national security concept, and there are relevant documents to guide security work in different fields. Among them, the ones that have strong relevance to the fields of data security and personal information protection are: the civil field has passed the “Civil Code”; in the field of cyberspace security, there are the “Cyber Security Law”, the Equal Guarantee 2.0 series of standards, and the “Cyber Security Review Measures” Etc.; in the field of data security: the “Data Security Law” has just been promulgated. In the field of personal information protection, the “Personal Information Protection Law” has just been promulgated. There are also special legislations in the fields of children’s personal information, passwords, cybercrime, consumer rights protection, and e-commerce. Generally speaking, the “Cyber Security Law”, “Data Security Law” and “Personal Information Protection Law” together constitute the three pillars of my country’s new data order under the framework of the overall national security concept.
2. Content interpretation
2.1 Overview
In the information age, the protection of personal information has become one of the most immediate and practical interests of the people. The “Personal Information Protection Law” adheres to and implements the people-centered concept of rule of law, firmly grasps the legislative positioning of protecting the people’s personal information rights and interests, and focuses on outstanding issues in the field of personal information protection and major concerns of the people.
The full text consists of eight chapters and seventy-four articles, clarifying the scope of application of the law, focusing on the current outstanding issues of personal information protection. On the basis of relevant laws, the law further refines and perfects the principles and personal information processing rules for personal information protection. , Clarify the boundaries of rights and obligations in personal information processing activities, and improve personal information protection working mechanisms. Establish personal information processing rules centered on “inform-consent”, implement the protection responsibilities of state agencies, and increase punishment for violations.
2.2 Seven key points
2.2.1 Definition of terms
The “Personal Information Protection Law” stipulates the definitions of three terms and the meanings of four related terms. This article only discusses the definitions or meanings of “personal information”, “sensitive personal information”, “processing of personal information” and “automated decision-making”. Further interpretation:
“Personal information” is defined in a way of “identification”, and only adopts a defined method. The published “Personal Information Security Regulations” has not fully enumerated. With the continuous development of the data economy, this article boldly predicts that the definition and scope of personal information will also be extended again.
“Sensitive personal information”, this statement is different from the “personal sensitive information” in the “Personal Information Security Regulations” but the content expressed is basically the same, but the “sensitive personal information” in this law emphasizes “personal dignity.” It is worth noting that this law has also made new additions and adjustments to the listed information: biometrics, religious beliefs, specific identities, medical and health, financial accounts, whereabouts and other information, as well as individuals under the age of fourteen. information.
“Handling of personal information”, compared with the first review of the draft, the main change lies in the deletion of “activities”, emphasizing the actions or scenarios of handling personal information.
“Automated decision-making”, the main change lies in the adjustment of the sequence of subject, predicate and object, emphasizing the impact of the important application of artificial intelligence technology on citizens’ personal information rights.
2.2.2 Scope of application
This law clarifies the two major scopes of application of “inside my country” and “overseas jurisdiction”. “Overseas jurisdiction” equally responds to the long-arm jurisdiction effect of foreign legislation such as the European Union’s GDPR and the United States’ CCPA.
Within the territory of my country: This law applies to the processing of personal information of natural persons within the territory of the People’s Republic of China.
Overseas jurisdiction: This law also applies to the processing of personal information of natural persons within the territory of the People’s Republic of China outside the People’s Republic of China under any of the following circumstances.
For the purpose of providing products or services to domestic natural persons;
Analyze and evaluate the behavior of natural persons in the territory;
Other circumstances stipulated by laws and administrative regulations.
2.2.3 Basic principles
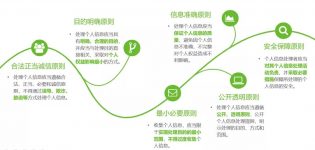
In the “Chapter 1 General Provisions” section, the basic principles of handling personal information are further clarified. This article refers to relevant laws and regulations, combined with corporate practices, and summarizes the following six basic principles.

2.2.4 Ecological integration of “point”, “surface” and “ball”
This article constructs a personal information protection ecological fusion system from “points”, “planes” and “spheres” to achieve mutual influence, mutual restraint, mutual trust, continuous evolution, and a relatively stable dynamic equilibrium state for a certain period of time.
“Point”: Refers to the protection of the whole people and adhere to the basic bottom line.
No organization or individual may illegally collect, use, process, or transmit the personal information of others, or illegally trade, provide, or disclose the personal information of others; and must not engage in personal information processing activities that endanger national security or public interest.
“Mian”: Refers to joint participation to build a benign ecology.
The state establishes a sound personal information protection system to prevent and punish violations of personal information rights and interests, strengthen personal information protection publicity and education, and promote the formation of a good environment for governments, enterprises, relevant social organizations, and the public to participate in personal information protection.
“Ball”: Refers to international cooperation to promote ecological integration.
The state actively participates in the formulation of international rules for personal information protection, promotes international exchanges and cooperation in personal information protection, and promotes mutual recognition of personal information protection rules and standards with other countries, regions, and international organizations.
2.2.5 Processing rules
Personal information processing rules: including general rules, rules for handling sensitive personal information, and special rules for handling personal information by state agencies. It should be noted that this law establishes personal information processing rules centered on “inform-consent”, and at the same time, it also adds exceptions for consent, such as the “previous paragraph” mentioned in Article 13 of the “Personal Information Protection Law”. Under the circumstances specified in items 2 to 7, no personal consent is required.”

Rules for the cross-border provision of personal information: This law establishes a set of clear and systematic rules for the cross-border flow of personal information to meet the objective requirements of protecting the rights and safety of personal information, and to meet the practical needs of international economic and trade exchanges. The detailed rules and requirements in cross-border provision scenarios are shown in the following figure:

2.2.6 Related entities
This law involves individuals, personal information processors, and supervisory authorities, which are three strong related entities. As shown in the figure below, it elaborates on personal rights, personal information processor obligations, and personal information protection duties performed by supervisory authorities.

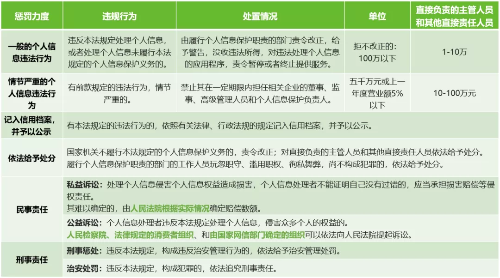
2.2.7 Strong supervision and punishment
In recent years, there has been an increase in the infringement of personal information rights and interests, such as the identification of “inform-consent”, personality rights disputes, face recognition, and other rights that are strongly related to personal information subjects. Therefore, this law strengthens supervision and punishment in this regard. This law provides for “general personal information violations” and “serious personal information violations”. Although there are no strict definitions and explanations on the two, you can refer to past judicial cases or use GDPR-related punishment cases. The detailed punishment requirements are shown in the figure below:
2.3 Horizontal comparison
In order to facilitate a further understanding of the “Personal Information Protection Law”, this article uses a tabular method to make a horizontal comparison of several domestic laws and regulations, as shown in the figure below. The comparison of this article is limited to the non-legal professional perspective, so in a strict sense, it cannot accurately compare and analyze the relevant issues of the legal effect level.
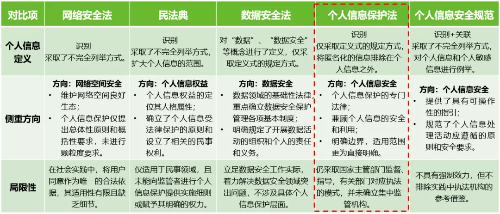
After horizontal comparison from the above three aspects of definition, focus on direction, and limitations, this article draws the following reference conclusions:
1) With the continuous improvement of my country’s laws and regulations, all walks of life need to consider the issue of “compliance” first, and especially need to pay attention to specific and achievable safety requirements;
2) The various laws and regulations have their own focus and have a certain degree of interrelationship, and special attention should be paid to the legal effect of the upper law; in the specific practice process, all need to be followed and implemented;
3) Both the “Data Security Law” and the “Personal Information Protection Law” put forward the implementation of the responsibilities and obligations of processors. For companies, is it necessary to establish two sets of standards? The answer is no. It is recommended to integrate them. Organizational construction and system processes can be combined into one. Personnel capabilities and technical measures need to be implemented in a targeted manner, and specific requirements should be refined and controlled.
2.4 Interpretation and thinking
2.4.1 Typical QA
Typical question 1: About “inform + agree”.
Basis: Article 14 uses “fully informed” as a prerequisite for “consent” and requires “individual consent”: Articles 23, 25, 26, 29, 39.
Answer: Obtain the authorized use of personal information through the user’s active check and browse the privacy policy, and give the user the right to withdraw consent; at the same time, sort out the scenarios of “individual consent” and adjust the corresponding functions.
Typical question 2: Regarding sensitive personal information such as biometrics.
Basis: The premise of “Personal images and identification information collected can only be used for the purpose of maintaining public safety” stipulated in Article 26, “specified purpose and sufficient necessity” stipulated in Article 28, and stipulated in Article 29 “Individual consent”, the notification of “necessity and impact on personal rights” stipulated in Article 30.
Answer: Pay attention to the handling rules of sensitive personal information, and do a good job of relevant and adequate notification and impact assessment.
Typical question 3: About the “person in charge of personal information protection”.
Basis: Article 52 stipulates that “personal information processors who process personal information up to the number prescribed by the national cyberspace administration shall designate a person in charge of personal information protection.”
Answer: The “prescribed number” is not clearly specified in this law, but you can refer to the provisions of the “Personal Information Security Regulations”: the number of employees is greater than 200, the processing of personal information of more than 1 million people, and the processing of more than 100,000 individuals Sensitive information.
Typical question 4: About impact assessment.
Basis: Article 55 stipulates that “in any of the following circumstances, the personal information processor shall conduct a personal information protection impact assessment in advance and record the processing situation.”
Answer: In accordance with the relevant requirements of the “Personal Information Security Regulations” and “Impact Assessment Guidelines”, carry out the implementation of personal information security impact assessments.
The above-mentioned issues are only the tip of the iceberg. It is recommended that organizations formulate corresponding security strategies based on their actual conditions and implement personal information protection responsibilities.
2.4.2 Main concerns
1) Clarify the responsibility system for personal information protection and implement full life cycle management and control responsibilities.
Content: Establish an organizational structure for personal information protection, clarify job responsibilities, and formulate corresponding full-process management specifications, systems, and procedures.
Program support: data security management system construction.
2) Realize the first step of construction through classification (grading) management of personal information.
Content: Establish a personal information management mechanism, clarify the protection objects and strategies.
Program support: data classification and classification.
3) Discover hidden dangers of corporate personal information security and reduce the risk of information leakage.
Content: Use risk assessment methods to identify and discover the personal information security risks of the company, assist the company in rectification, and improve the level of protection of the company’s personal information.
Program support: personal information security impact assessment, APP personal information security assessment.
4) Identify personal information processing activities and implement security technical measures.
Content: sorting out the processing activities of personal information throughout the life cycle, formulating corresponding security requirements, reminding each risk point, including mechanisms that can be implemented.
Program support: special planning for personal information protection, data security management and control platform.
5) Establish an emergency response mechanism for personal information security incidents.
Content: Establish a personal information security emergency response plan, clarify the emergency guidelines, policies, emergency organization structure and related emergency responsibilities for personal information incidents.
Program support: construction of emergency response system.
6) Organize and carry out personal information security training and education.
Content: Organize and carry out personal information security professional training, enhance the awareness of personal information security protection of enterprises and institutions, and strengthen the professional ability of personal information security personnel.
Program support: professional education and training of personal information security.
7) Focus on cross-border provision of personal information to protect national security, public interests and personal rights.
Content: Establish the full-process management norms, systems, and procedures for cross-border provision of personal information; clarify the compliance path and obtain the individual consent of users to ensure the safe circulation of personal information.
Program support: Follow the relevant national regulations on the export of personal information.
3. Summary and Outlook
2021 can be said to be the first year of data protection. The promulgation and imminent implementation of a series of laws and regulations such as the Data Security Law, the Personal Information Protection Law, the Critical Information Infrastructure Security Protection Regulation (State Council Order No. 745), and the Data security and personal information protection have officially entered the 2.0 era. Data security and personal information protection are inseparable, just like twin brothers. With regard to the countermeasures of personal information protection, special design and implementation can be carried out on the basis of data security construction to form a long-term mechanism for personal information protection system (IRCSS). This mechanism mainly uses five aspects to implement personal information security landing construction, helping organizations establish management systems and operating procedures, fully understand personal information security conditions, improve personal information security monitoring and protection measures, and achieve continuous self-adaptation through optimization, improvement and continuous operation Personal information security protection capabilities.

4. Scene discussion: “Double Eleven” online shopping spree
In recent years, the “Double Eleven” online shopping spree has also been the peak of personal information leakage. The “Personal Information Protection Law” will also come into effect on November 1, 2021. In the face of this year’s “Double Eleven”, how consumers, businesses, Internet platform operators, regulatory authorities, etc. should use the “Personal Information Protection Law” How to fulfill the responsibilities stipulated in the “Personal Information Protection Law” for the rights and interests granted? Next, this article tries to think about how to face it from the perspective of these four types of subjects.
The Links: LM150X08-A4K8 CM75DUM-12F


